Azure deployment
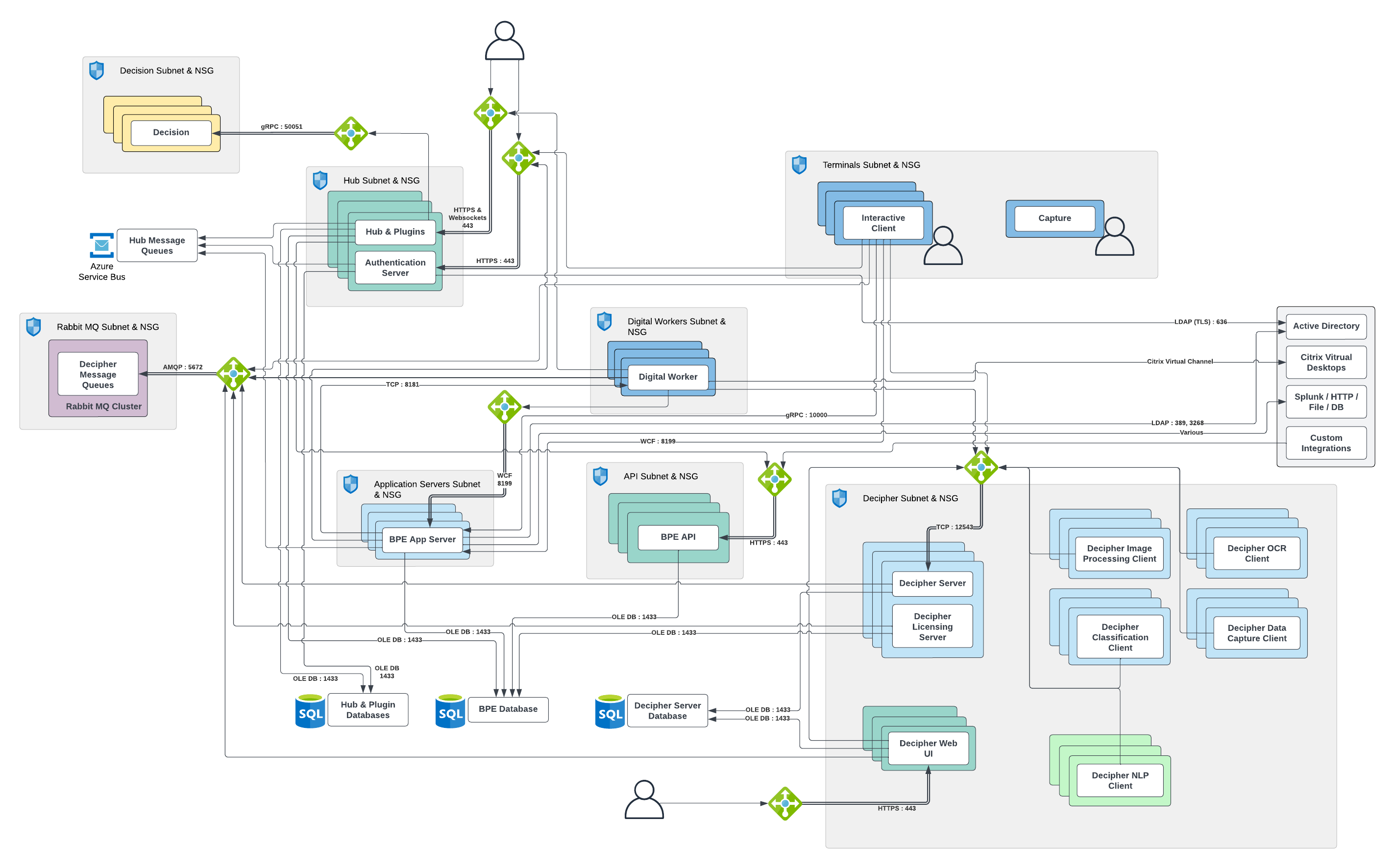
In the Azure deployment pattern, several SS&C Blue Prism components are replaced with Azure platform services, such as Azure Service Bus, Azure SQL databases, and Azure load balancers. Additionally, a logical division of components into Azure subnets is proposed to facilitate network security routing and permissions. All of these adaptations are optional and flexible, in that it is possible to vary the subnets, and mix and match platform services with native versions to suit business requirements.
It is not possible for SS&C Blue Prism to test and validate every deployment variation for every scale. The deployment patterns used as an example in this guide illustrate how the products are designed to work together to support customer architects and deployment engineers in making informed decisions. It should not be assumed that they can be followed exactly, nor that they will be appropriate for every real-world use case. It is expected that organizations will apply appropriate expertise to adapt and vary these designs to fit their own needs.
Network considerations
It is assumed that all components will be in a single Azure Vnet, and that this can be extended with VPN connections. Alternatively, it would also be possible to use a separate Vnet for Decipher IDP, with Decipher components divided into subnets as required, and peered to the main Blue Prism Vnet.
No external RDP connections are included, but again this is flexible to suit business requirements, for example using a jump box, bastion host, or just-in-time (JIT) VM access. Likewise, either Service Endpoints or Private Links can be used for databases, Azure Service Bus, or other infrastructure.
High availability and load balancers
Duplicates of all Blue Prism components can be installed to provide redundancy, although the requirement for this will depend on business SLAs and whether the Azure platform SLAs are sufficient without additional resiliency. When deployed this way all components are in active-active patterns, and load balancers are frequently required for network connections to resolve across multiple instances of the same component (see AWS deployment network architecture for the positioning of these). All load balancers can be Azure load balancers or software load balancers; the Blue Prism application server load balancer requires a session affinity setup.
Machine types and platform services
All Windows server and Windows desktop machines can be selected from appropriate virtual machine SKUs, and likewise the container platform for Decision is completely flexible, for example virtual machines, container instances, Azure Kubernetes Service, or similar.
It is possible for Hub to use Azure Service Bus or any other AMQP-compliant message bus, however Decipher IDP requires RabbitMQ as its message bus.
Azure deployment component breakdown
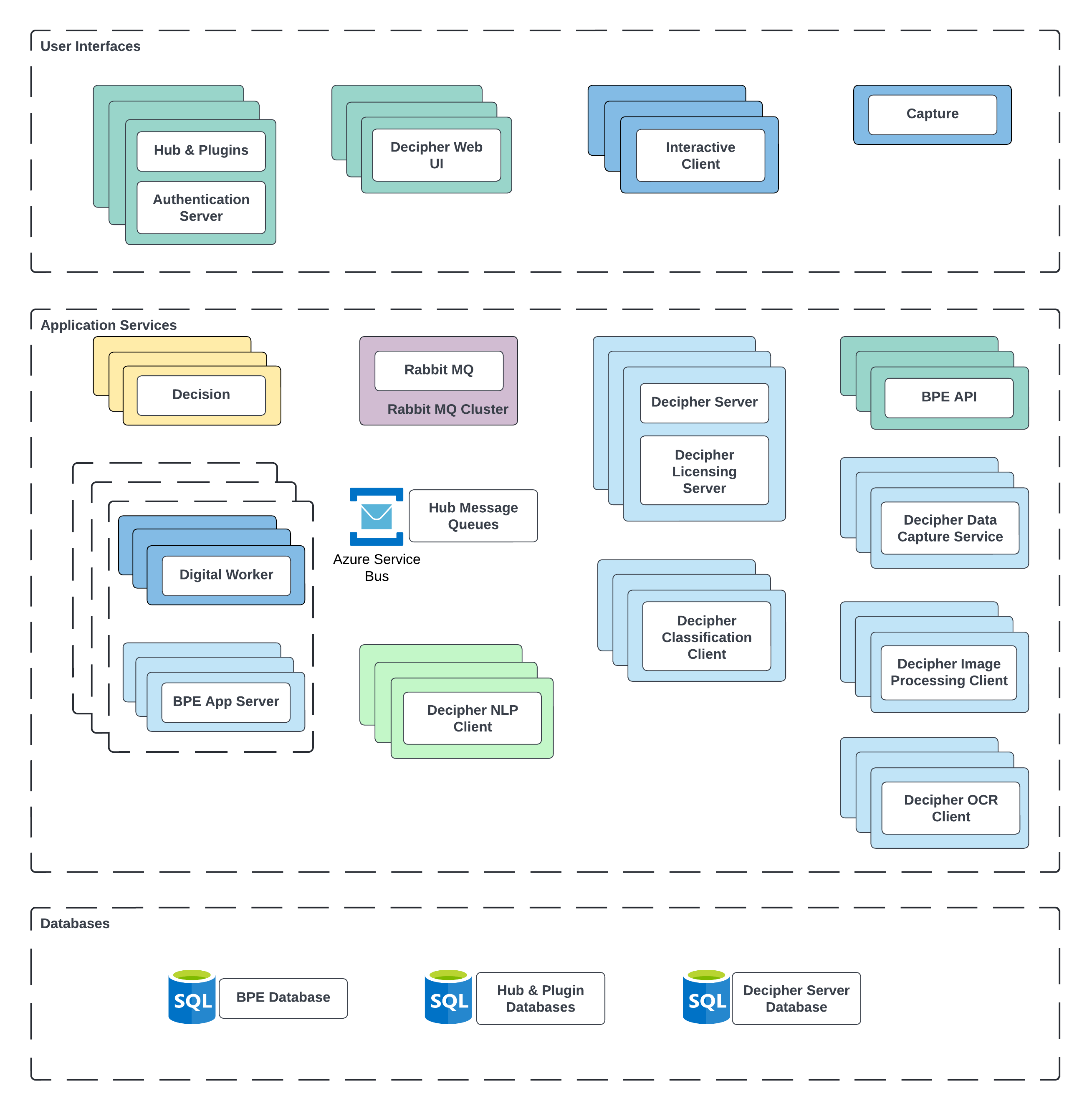
Azure deployment network architecture
The following diagram illustrates an Azure deployment network architecture that includes SS&C Blue Prism Enterprise, Blue Prism Capture, Blue Prism Decipher IDP, Blue Prism Decision, Blue Prism Hub, Blue Prism Interact, and Blue Prism Authentication Server deployments. Click here to view the accompanying legend.
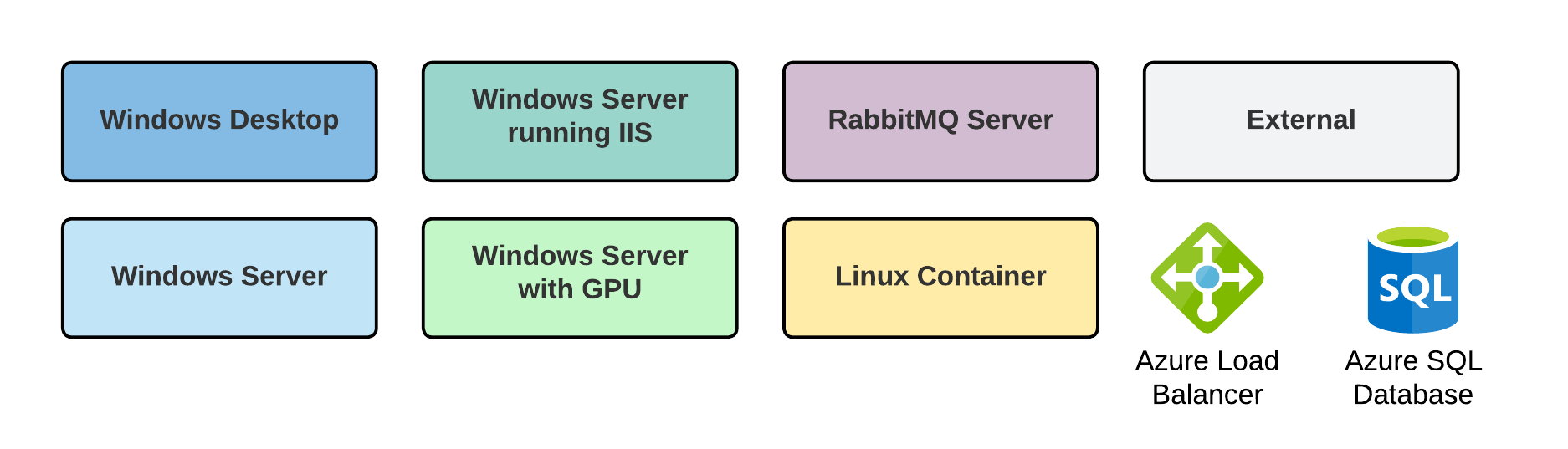
Network architecture diagram legend
 Docs
Docs